
AI TACTICAL SKILLS
CYBER SKILLS ACADEMY
"Learning by Doing" approach equips participants with the critical skills needed to excel in the dynamic field of AI / ML and cybersecurity.

ONLINE │ IN PERSON / HYBRID │ GLOBALLY DELIVERED
LEARNING BY DOING
The Tactical Industry Cyber Skills Academy (TICSA) offers an innovative,
hands-on approach to cybersecurity education. Our "Learning by Doing"
methodology ensures that participants gain practical, real-world skills
essential for defending against modern cyber threats. This immersive
training model is designed to prepare professionals for immediate
application of their skills in the industry, bridging the gap between
theoretical knowledge and practical expertise.
Academy Highlights
Benefits of “Learning by Doing” Approach
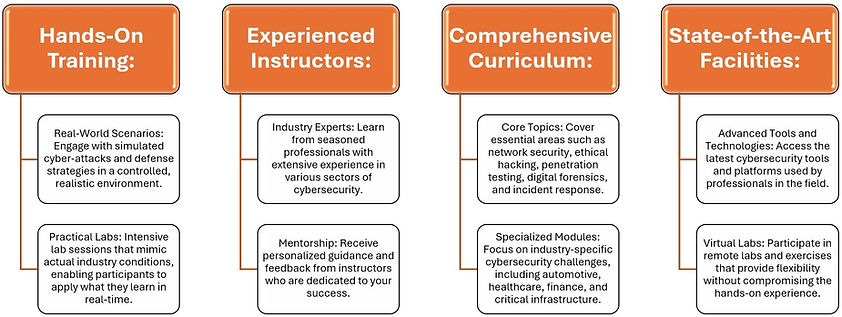



Conclusion
By combining hands-on training, expert instruction, and a comprehensive curriculum, TICSA prepares cybersecurity professionals to meet the challenges
of today’s digital landscape and secure the systems of tomorrow.
CONTACT CYBER2 LABS
USA: +1 310 601 8570
27762 Palos Verdes Dr E,
Rancho Palos Verdes, CA 90275






